ISP vs VPN vs Tor
I've seen way too many comments about people using VPNs and/or Tor as a shield to any kind of possible breach of privacy and/or security in general. I'm going to attempt to explain very simply what they do, because these are good tools, but using them the wrong way can void their purpose.
Vanilla Internet
This is what things look like when using the Internet without VPN, Tor or proxies.
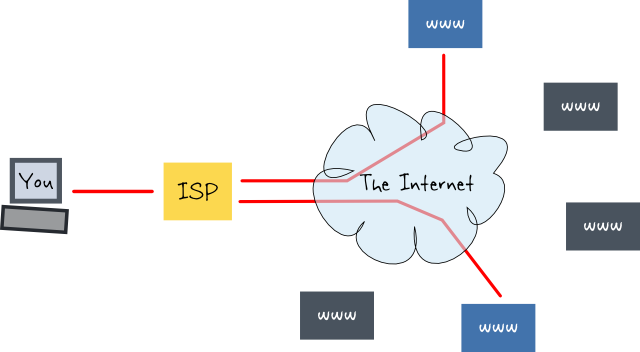
In red is regular Internet traffic. This goes directly from you to the websites (and other resources) you connect to, and back. Your ISP transmits all your Internet packets for you.
Sometimes the traffic is encrypted (HTTPS, TLS, etc), but many times it is not. When it's not, everything being sent is visible to the ISP.
TL;DR The ISP knows where you are connecting to and can read all your unencrypted traffic.
VPN Router
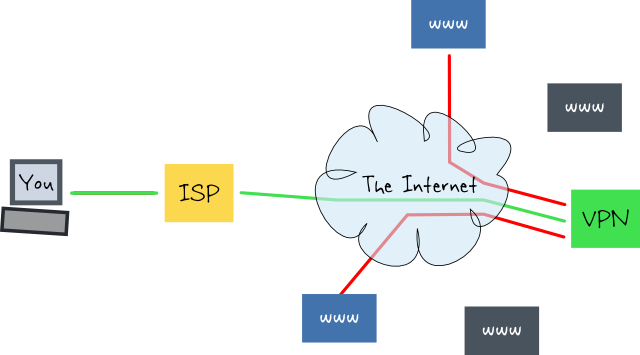
A VPN router will create a tunnel between you and itself. Once the tunnel is up, your computer should send all its Internet traffic through that tunnel. The tunnel goes through your ISP, but because the tunnel is encrypted (I hope so), your ISP should only see that you are connected to the VPN.
Once your traffic reaches the VPN server, everything after that is as usual (red). This means that whatever your ISP could see in the previous case, your VPN provider can now see.
TL;DR The VPN router knows where you are connecting to and can see all unencrypted traffic just like your ISP in the vanilla scenario, and your ISP knows you're using the VPN.
Tor (the) Onion Router
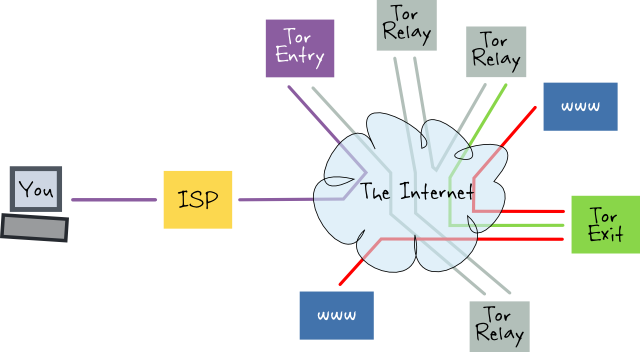
Imagine Tor as being like a VPN router except that its entry and exit points are separate systems and in between there are a bunch of Tor relay nodes that are also separate systems. The purpose of Tor is to route traffic so that each node only knows of the previous and next hop, in other words, to allow untraceable connections.
The traffic itself is encrypted all the way up to the exit node. From there on the same rules apply as with your ISP in the first case and the VPN in the second. Whatever is not encrypted is visible and connection destinations are known. What shouldn't be known to the exit node is the origin of the traffic, you.
One way of doing it wrong would be if you make insecure connections to personal resources (or even secure connections to personal resources), the exit node can guess who you really are. Once it does that, it can then link your other activities back to you.
The strength and weakness of Tor is linked to the amount of nodes operated by independent entities. Imagine the Tor network like a connect the dots puzzle, each node can see 3 dots (previous, next and current hops). If one entity operates enough nodes then they can draw themselves a clearer picture of what is happening.
In other words The ISP knows you are using Tor, that's all they should see.
TL;DR Your ISP knows you are connected to the Tor network and the Tor exit node can see all your traffic just like in the previous cases. However the exit node shouldn't be able to trace the connection back to you.
Why ? And if so, Which One ?
Once you understand what these things do and what they don't do you should be able to decide for yourself when, where and which. You might also start to prefer using HTTPS and other forms of encryption for any communication because as we've seen, whatever you do, if it's in cleartext, someone can read it.
There are always a few easy reasons to use such things, for example censorship circumvention. Most Internet censorship happens at the ISP, bypassing them can help get around it and for that, a VPN should suffice. If you want to greatly reduce the possibility of tracing the connection back to you, Tor would be better.
Sometimes BT (British Telecom) impersonates websites you visit and displays a fake "404 page not found" error when they should be displaying a page explaining that the website you are trying to reach has been censored. Even Saudi Arabia is more open about what sites are actually censored.
Other reasons may be more technical, for example, more and more ISPs enjoy messing with how the Internet is designed to function. For example, TalkTalk hijacks DNS queries so the results you get aren't real anymore. According to TalkTalk there's no such thing as a non existing DNS record. This isn't even related to banning content, it's just plain tampering with communications and is probably illegal.
There could even be routing issues. For example at some point when in France, when using "Free" (ISP), everything on Youtube would lag because of some dispute between Free and Google. Using a VPN helped get a better route.
Temporary Fixes Shouldn't Become the Norm
Treat your VPN provider like an ISP. Unless you are personally running the VPN server on dedicated hardware, you cannot trust them to not keep logs and do other nasty things. It also helps if you know the network administrator....
These solutions, as well as others (proxies and so on) should be considered temporary. As soon as they become a problem there will be attempts to block users from employing them.

